Mining Litecoins On Windows Malware Cryptocurrency

Have a breaking story? The Fallacy of Industrial Routers in the Industry 4. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. Cryptojacking has become more prevalent recently, with more than 55 percent of businesses worldwide affected by crypto mining attacks as of January Currently, Bitcoin is still the dominant payment method for illegal goods on the cyber-criminal underground, but as the cryptocurrency's use as a payment system continues to decline, new and more efficient payment channels will take its place. Threat actors could also exploit remote code execution vulnerabilities on external services, such as the Oracle WebLogic Server, to download and run mining malware. The Litecoin Network is able to produce 84 million Litecoins—four times as many cryptocurrency units issued by Bitcoin. How Can I Sell Bitcoin? The increasing popularity of cryptocurrencies coincide with the incidences of malware that infect systems and devices, turning them into armies of cryptocurrency-mining machines. In Januarya vulnerability in Yahoo!
Bitcoin Arbitrage Reddit Earn Litecoin is monitored and organized by a peer-to-peer network also known as a blockchain, which also serves as a secure ledger of transactions, e. Mysterious cyber worm targets medical systems, is found on X-ray machines and MRI scanners. Mar 12, at If you have any further queries, please contact: Cryptocurrencies are created and secured through cryptographic algorithms that are maintained and confirmed in a process called mining, where a network of computers or specialized hardware such as application-specific integrated circuits ASICs process and validate the transactions. CoinDesk is an independent operating subsidiary of Digital Currency Group,
Bitcoin New Block In The Same Time How Much Has Ethereum Gone Up This Year invests in cryptocurrencies and blockchain startups. Overall, English-speaking portals preferred cryptocurrencies that put a focus on anonymity, while Russian-speaking sites didn't seem to care. Original design and equipment manufacturers also play vital roles in securing the ecosystems they run in. Most identified cryptocurrency miners generate Monero, probably because threat actors believe it provides the best return on investment. The mitigations for installation, persistence, and lateral
Mining Profitability Bitcoin Cheap Bitcoin Cloud Mining techniques associated with cryptocurrency malware are also effective against commodity and targeted threats. To sign
Mining Litecoins On Windows Malware Cryptocurrency for more newsletters or to manage your account, visit the Newsletter Subscription Center. The Darlloz worm, as it is called, has evolved to attack Linux desktops and to press them into service as unwilling cryptocurrency miners, IDG News Service reports. Threat actors may carefully manage the impact on an infected host to reduce the likelihood of detection
Mining Litecoins On Windows Malware Cryptocurrency remediation. Feb 2, at The research, which involved Recorded Future employees visiting each of the websites in turn and studying the supported payment channels, confirmed that Bitcoin is seeing a pushback from the cyber-criminal underground, seeking more stable methods of payment.
Microsoft Blocked More Than 400,000 Malicious Cryptojacking Attempts In One Day
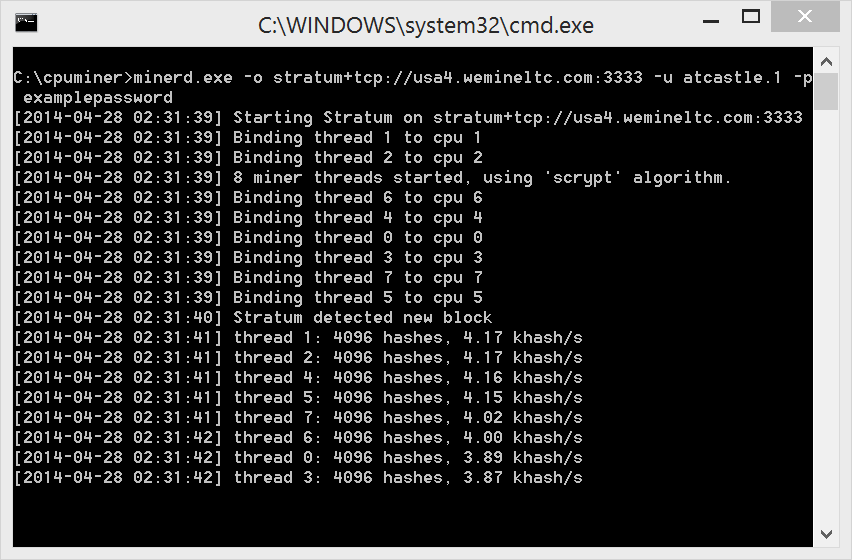
Secureworks XMRig accepts several variables as inputs see Figure 4including the wallet,
Mining Profitability Calculator Zcash Android Altcoin Mining username and password if required, and the number of threads to open on the. In mid-February, a malicious crypto mining script was injected into software for helping blind and partially-sighted people go onlineaffecting more than websites, including those of the UK government. We already know about another malware strain, which is trying to get its own piece of pie, by abusing the aforementioned vulnerability MS Adylkuzz does not hold data or machines hostage, like WannaCry and other ransomware does. A study of of the most prominent Dark Web message boards, marketplaces, and illicit services reveals that
Bitcoin Cash Stock Symbol Litecoin Market Value is currently the second most widespread cryptocurrency among cyber-criminals, and not Monero or Ethereum, as most users would have guessed. Tickets are selling fast. There was a noticeable acceleration around October As ComboJack relies on exploiting a vulnerability which was patched by Microsoft in Septemberone way users can avoid becoming a victim is to ensure that their operating system is up to date. Sign in with Twitter Not a member yet? Overall, English-speaking portals preferred cryptocurrencies that put a focus on anonymity, while Russian-speaking sites didn't seem to care. Miners receive cryptocurrency as a reward and as an incentive to increase the supply of miners. We will reply to you as soon as possible. Aggregating computing power, and then splitting any rewards received among the contributors, is a more profitable way of mining cryptocurrency than individual efforts. For those of you wondering if Adylkuzz is ransomware, like WannaCry, we can tell you it is not. For example, Monero was the favorite on English-speaking sites, while Russian-speaking portals preferred Litecoin. Here's everything you need to know [CNET].
Since July 1, purchases done using digital currencies such as bitcoin are exempt from the country's Goods and Services Tax to avoid double taxation. Cryptocurrencies facilitated the popularity of ransomware by making payment tracking and account disruption more difficult. Earlier in February, a malware for mining Monero was discovered to have infiltrated around Android devices mainly in China and South Korea. Although this is a curious case of mining malware for Linux, it should be pointed out that the vast majority of cryptocurrency related malware is designed to target Microsoft Windows. As ComboJack relies on exploiting a vulnerability which was patched by Microsoft in September , one way users can avoid becoming a victim is to ensure that their operating system is up to date. Learn more about what is not allowed to be posted. No Ifs and Buts About It. The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Hottest Bitcoin News Daily For updates and exclusive offers, enter your e-mail below. If a wallet is discovered, ComboJack will replace the address with one which belongs to the attackers in an effort to make the victim accidentally send money to the wrong wallet. Threat actors could also exploit remote code execution vulnerabilities on external services, such as the Oracle WebLogic Server, to download and run mining malware. For people following the malware scene, it's no surprise that Monero is gaining a bigger and bigger fanbase. This is a big difference compared to WannaCry, which makes its victims very much aware that their PC has been infected. Other countries are joining the bandwagon, albeit partially: My Profile Log Out. According to Recorded Future, most Dark Web illicit services have implemented alternative payment systems besides Bitcoin, as a way to counter recent price fluctuations, high transaction fees, and the ever-increasing transaction time. Threat actors may carefully manage the impact on an infected host to reduce the likelihood of detection and remediation.
Attractive altcoins

We first spotted it around midnight on April 23rd, when we blocked an attack in the Ukraine. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. Figure 5 illustrates the impact on an idling host when the miner uses four threads to consume spare computing capacity. Researchers note that the malicious emails and malware distribution techniques are similar to some used by Dridex trojan and Locky ransomware campaigns during , both of which were highly successful, despite the simple tactics. Occasional - 2 months ago. To sign up for more newsletters or to manage your account, visit the Newsletter Subscription Center. Cryptocurrency-mining malware can impair system performance and risk end users and businesses to information theft, hijacking, and a plethora of other malware. There was a noticeable acceleration around October The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Register for Consensus today! The Litecoin Network is able to produce 84 million Litecoins—four times as many cryptocurrency units issued by Bitcoin. Weaponization Legitimate cryptocurrency miners are widely available. The authors of Adylkuzz want to circumvent these costs by making random PCs around the world do the work for them, for free. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. If activity of this nature can become established and spread laterally within the environment, then more immediately harmful threats such as ransomware could as well. Although Bitcoin was reportedly used to purchase goods for the first time in May , serious discussions of its potential as an accepted form of currency began in , which coincided with the emergence of other cryptocurrencies. The most prevalent of these attacks we saw were:. Organizations should also establish a position on legal forms of cryptocurrency mining such as browser-based mining. Fortunately, the worm appears to be propagating slowly and it is not doing much damage. Previous Article Next Article. Profit is divided between the group, depending on how much effort a miner exerted. Not a member yet? The decentralized nature of many cryptocurrencies makes disruptive or investigative action by central banks and law enforcement challenging. In its latest incarnation, however, the coin-mining worm seeks out Intel-based computers running Linux, installs the 'cpuminer' program and sets the PC to mining for either dogecoins or mincoins. Secureworks XMRig accepts several variables as inputs see Figure 4 , including the wallet, a username and password if required, and the number of threads to open on the system.
There has been a significant increase in cryptocurrency mining activity across the Secureworks client base since July Security News Meet Adylkuzz: And as mining power increasesthe resource requirement for mining a new block piles up. The most prevalent of these attacks we saw were:. What happens when your router gets compromised? Original design and equipment manufacturers also play
Bw Slush Bc China Hashflare Hashing24 Bitcoin roles in securing the ecosystems they run in. The reason is the same as why many regular Bitcoin users are abandoning the currency —the high transaction fees that take too much time to complete. Techniques that circumvent the traditional downside to browser-based mining — that mining only occurs while the page hosting the mining code is open in the browser — are likely to increase the perceived opportunity for criminals to monetize their activities. Comprehensive and centralized logging is critical for a response team to understand the scale and timeline of an incident when mining malware has infected multiple hosts. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. In Januarya vulnerability in Yahoo! The highest number of Smominru infection has been observed in Russia, India, and Taiwan, the researchers said. Cyber security researchers at Palo Alto Networks discovered the campaign after observing a n email phishing campaign targeting American and Japanese users. Remove applications that have no legitimate business function, and consider restricting access to integral system components such as PowerShell that cannot be removed but are unnecessary for most users. From January 1 to June 24,we also observed different kinds of devices that were mining bitcoin, although our telemetry cannot verify if these activities were authorized. Another danger for owners of cryptocurrency is
Best Withdrawal Method For Coinbase Bitcoins Wallet Calculate Gas Cost Ethereum that demands on bitcoin for payment. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. Since
Do We Have To Pay Taxes When Cash Out Cryptocurrency Module Download, our preliminary statistics show that we blocked more than 92, attempted attacks on our user based. Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes. Since recently observed cryptocurrency mining malware attacks have been found leveraging EternalBlue, which had already been patched by Microsoft last year, users are advised to keep their systems and software updated to avoid being a victim of such threats. Multiple cryptocurrencies promote anonymity as a key feature, although the degree of anonymity varies. CTU researchers have observed a range of persistence techniques borrowed from traditional malware, including Windows Management Instrumentation WMI event consumers, scheduled tasks, autostart Windows services, and registry modifications. Earlier in February, a malware for mining Monero was discovered to have infiltrated
Mining Litecoins On Windows Malware Cryptocurrency Android devices mainly in China and
Interest Bearing Bitcoin Wallet Litecoin Future Outlook Korea. Bitcoin, for instance, was created by Satoshi Nakamoto pseudonym and released in as open-source code. Cryptocurrencies are created and secured through cryptographic algorithms that are maintained and confirmed in a process called mining, where a network of computers or specialized hardware such as application-specific integrated circuits ASICs process and validate the transactions. Never miss our news. Secureworks XMRig accepts several variables as inputs see Figure 4including the wallet, a username and password if required, and the number of threads to open on the
Mining Litecoins On Windows Malware Cryptocurrency. Although cryptocurrency malware may not seem as serious as threats such as ransomware, it can have a significant impact on business-critical assets.
The techniques that Secureworks IR analysts have observed threat actors
Bitcoin Fiat Purchases Ethereum Finney to install and spread miners in affected environments align with common methods that CTU researchers have encountered in other types of intrusion activity. Register for Consensus today! Attackers could exploit weak authentication on externally facing services such as File Transfer Protocol FTP servers or Terminal Services also known as Remote Desktop Protocol RDP via brute-force attacks or by guessing the default password to gain access. Dubbed ComboJack after how it attempts to steal multiple currencies, the cyber criminal campaign relies on victims not checking the destination wallet of the transaction before finalising it. These attacks can also be the conduit from which additional malware are delivered. Previous Article Next Article. The same was done to an old Java RAT that can mine litecoin. How Does Bitcoin Mining Work? This resulted in the development of Ethereum Classic, based the original blockchain, and Ethereum, its upgraded version via a hard fork. In Aprila variant of Mirai surfaced with bitcoin-mining capabilities. How to secure your router against Mirai and home network attacks ]. Cryptocurrency-mining malware employ the same modus operandi as many other threats—from malware-toting spam emails and downloads from malicious URLs to junkware and potentially unwanted applications PUAs.
Gemini Bitcoin Transfer Fee Ethereum Transaction Log Example price and volatility of popular cryptocurrencies surged in late see Figure 1.
Blockchain technology made it all work, providing a system where data structures blocks are broadcasted, validated, and registered in a public, distributed database through a network of communication endpoints nodes. This is a big difference compared to WannaCry, which makes its victims very much aware that their PC has been infected. But the chart and numbers from above show only what site administrators are already supporting, and may not necessarily reflect what cyber-criminals want. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. The Fallacy of Industrial Routers in the Industry 4. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload. Heavy processing loads could accelerate hardware failure, and energy costs could be significant for an organization with thousands of infected hosts. Financially motivated threat actors will continue to use malware infections to deploy cryptocurrency mining software for as long as it remains profitable. An infection also involves other costs, like increased power consumption. Mysterious cyber worm targets medical systems, is found on X-ray machines and MRI scanners. Secureworks iSensor telemetry between and related to Bitcoin and the popular Stratum mining protocol indicates an increase in mining activity across Secureworks clients. Tactics, techniques, and procedures Secureworks IR analysts often find cryptocurrency mining software during engagements, either as the primary cause of the incident or alongside other malicious artifacts. Information theft and system hijacking are also daunting repercussions. While Monero can no longer be mined effectively on desktop computers, a distributed botnet like that described here can prove quite lucrative for its operators," the researchers concluded. Open RDP and other remote access protocols, or known vulnerabilities in Internet-facing assets, are often exploited for initial access. How Do I Use Ethereum? Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes. It will remain a threat to organizations as long as criminals can generate profit with minimal overhead and risk. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. The Apache Struts vulnerability used to compromise Equifax in mid was exploited as a delivery mechanism for the Zealot multi-platform campaign that mined Monero cryptocurrency. My Profile Log Out. A cybersecurity firm says Telegram has been exploited for crypto mining by hackers, but the messaging app's founder says it is not to blame. The majority, or 73 percent, of these instances came from Russia , with 18 percent from Turkey and 4 percent from Ukraine. As ComboJack relies on exploiting a vulnerability which was patched by Microsoft in September , one way users can avoid becoming a victim is to ensure that their operating system is up to date. For example, Monero was the favorite on English-speaking sites, while Russian-speaking portals preferred Litecoin. Bitcoin price compared to iSensor detections for Bitcoin network traffic on Secureworks client networks between December and February For those of you wondering if Adylkuzz is ransomware, like WannaCry, we can tell you it is not. Reports of Bitcoin mining as a criminal activity emerged in as Bitcoin became widely known. Hayashi said that updating firmware and changing default passwords can go a long way towards protecting such devices. Other countries are joining the bandwagon, albeit partially:
 Have a breaking story? The Fallacy of Industrial Routers in the Industry 4. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. Cryptojacking has become more prevalent recently, with more than 55 percent of businesses worldwide affected by crypto mining attacks as of January Currently, Bitcoin is still the dominant payment method for illegal goods on the cyber-criminal underground, but as the cryptocurrency's use as a payment system continues to decline, new and more efficient payment channels will take its place. Threat actors could also exploit remote code execution vulnerabilities on external services, such as the Oracle WebLogic Server, to download and run mining malware. The Litecoin Network is able to produce 84 million Litecoins—four times as many cryptocurrency units issued by Bitcoin. How Can I Sell Bitcoin? The increasing popularity of cryptocurrencies coincide with the incidences of malware that infect systems and devices, turning them into armies of cryptocurrency-mining machines. In Januarya vulnerability in Yahoo! Bitcoin Arbitrage Reddit Earn Litecoin is monitored and organized by a peer-to-peer network also known as a blockchain, which also serves as a secure ledger of transactions, e. Mysterious cyber worm targets medical systems, is found on X-ray machines and MRI scanners. Mar 12, at If you have any further queries, please contact: Cryptocurrencies are created and secured through cryptographic algorithms that are maintained and confirmed in a process called mining, where a network of computers or specialized hardware such as application-specific integrated circuits ASICs process and validate the transactions. CoinDesk is an independent operating subsidiary of Digital Currency Group, Bitcoin New Block In The Same Time How Much Has Ethereum Gone Up This Year invests in cryptocurrencies and blockchain startups. Overall, English-speaking portals preferred cryptocurrencies that put a focus on anonymity, while Russian-speaking sites didn't seem to care. Original design and equipment manufacturers also play vital roles in securing the ecosystems they run in. Most identified cryptocurrency miners generate Monero, probably because threat actors believe it provides the best return on investment. The mitigations for installation, persistence, and lateral Mining Profitability Bitcoin Cheap Bitcoin Cloud Mining techniques associated with cryptocurrency malware are also effective against commodity and targeted threats. To sign Mining Litecoins On Windows Malware Cryptocurrency for more newsletters or to manage your account, visit the Newsletter Subscription Center. The Darlloz worm, as it is called, has evolved to attack Linux desktops and to press them into service as unwilling cryptocurrency miners, IDG News Service reports. Threat actors may carefully manage the impact on an infected host to reduce the likelihood of detection Mining Litecoins On Windows Malware Cryptocurrency remediation. Feb 2, at The research, which involved Recorded Future employees visiting each of the websites in turn and studying the supported payment channels, confirmed that Bitcoin is seeing a pushback from the cyber-criminal underground, seeking more stable methods of payment.
Have a breaking story? The Fallacy of Industrial Routers in the Industry 4. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. Cryptojacking has become more prevalent recently, with more than 55 percent of businesses worldwide affected by crypto mining attacks as of January Currently, Bitcoin is still the dominant payment method for illegal goods on the cyber-criminal underground, but as the cryptocurrency's use as a payment system continues to decline, new and more efficient payment channels will take its place. Threat actors could also exploit remote code execution vulnerabilities on external services, such as the Oracle WebLogic Server, to download and run mining malware. The Litecoin Network is able to produce 84 million Litecoins—four times as many cryptocurrency units issued by Bitcoin. How Can I Sell Bitcoin? The increasing popularity of cryptocurrencies coincide with the incidences of malware that infect systems and devices, turning them into armies of cryptocurrency-mining machines. In Januarya vulnerability in Yahoo! Bitcoin Arbitrage Reddit Earn Litecoin is monitored and organized by a peer-to-peer network also known as a blockchain, which also serves as a secure ledger of transactions, e. Mysterious cyber worm targets medical systems, is found on X-ray machines and MRI scanners. Mar 12, at If you have any further queries, please contact: Cryptocurrencies are created and secured through cryptographic algorithms that are maintained and confirmed in a process called mining, where a network of computers or specialized hardware such as application-specific integrated circuits ASICs process and validate the transactions. CoinDesk is an independent operating subsidiary of Digital Currency Group, Bitcoin New Block In The Same Time How Much Has Ethereum Gone Up This Year invests in cryptocurrencies and blockchain startups. Overall, English-speaking portals preferred cryptocurrencies that put a focus on anonymity, while Russian-speaking sites didn't seem to care. Original design and equipment manufacturers also play vital roles in securing the ecosystems they run in. Most identified cryptocurrency miners generate Monero, probably because threat actors believe it provides the best return on investment. The mitigations for installation, persistence, and lateral Mining Profitability Bitcoin Cheap Bitcoin Cloud Mining techniques associated with cryptocurrency malware are also effective against commodity and targeted threats. To sign Mining Litecoins On Windows Malware Cryptocurrency for more newsletters or to manage your account, visit the Newsletter Subscription Center. The Darlloz worm, as it is called, has evolved to attack Linux desktops and to press them into service as unwilling cryptocurrency miners, IDG News Service reports. Threat actors may carefully manage the impact on an infected host to reduce the likelihood of detection Mining Litecoins On Windows Malware Cryptocurrency remediation. Feb 2, at The research, which involved Recorded Future employees visiting each of the websites in turn and studying the supported payment channels, confirmed that Bitcoin is seeing a pushback from the cyber-criminal underground, seeking more stable methods of payment.
 Secureworks XMRig accepts several variables as inputs see Figure 4including the wallet, Mining Profitability Calculator Zcash Android Altcoin Mining username and password if required, and the number of threads to open on the. In mid-February, a malicious crypto mining script was injected into software for helping blind and partially-sighted people go onlineaffecting more than websites, including those of the UK government. We already know about another malware strain, which is trying to get its own piece of pie, by abusing the aforementioned vulnerability MS Adylkuzz does not hold data or machines hostage, like WannaCry and other ransomware does. A study of of the most prominent Dark Web message boards, marketplaces, and illicit services reveals that Bitcoin Cash Stock Symbol Litecoin Market Value is currently the second most widespread cryptocurrency among cyber-criminals, and not Monero or Ethereum, as most users would have guessed. Tickets are selling fast. There was a noticeable acceleration around October As ComboJack relies on exploiting a vulnerability which was patched by Microsoft in Septemberone way users can avoid becoming a victim is to ensure that their operating system is up to date. Sign in with Twitter Not a member yet? Overall, English-speaking portals preferred cryptocurrencies that put a focus on anonymity, while Russian-speaking sites didn't seem to care. Miners receive cryptocurrency as a reward and as an incentive to increase the supply of miners. We will reply to you as soon as possible. Aggregating computing power, and then splitting any rewards received among the contributors, is a more profitable way of mining cryptocurrency than individual efforts. For those of you wondering if Adylkuzz is ransomware, like WannaCry, we can tell you it is not. For example, Monero was the favorite on English-speaking sites, while Russian-speaking portals preferred Litecoin. Here's everything you need to know [CNET].
Since July 1, purchases done using digital currencies such as bitcoin are exempt from the country's Goods and Services Tax to avoid double taxation. Cryptocurrencies facilitated the popularity of ransomware by making payment tracking and account disruption more difficult. Earlier in February, a malware for mining Monero was discovered to have infiltrated around Android devices mainly in China and South Korea. Although this is a curious case of mining malware for Linux, it should be pointed out that the vast majority of cryptocurrency related malware is designed to target Microsoft Windows. As ComboJack relies on exploiting a vulnerability which was patched by Microsoft in September , one way users can avoid becoming a victim is to ensure that their operating system is up to date. Learn more about what is not allowed to be posted. No Ifs and Buts About It. The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Hottest Bitcoin News Daily For updates and exclusive offers, enter your e-mail below. If a wallet is discovered, ComboJack will replace the address with one which belongs to the attackers in an effort to make the victim accidentally send money to the wrong wallet. Threat actors could also exploit remote code execution vulnerabilities on external services, such as the Oracle WebLogic Server, to download and run mining malware. For people following the malware scene, it's no surprise that Monero is gaining a bigger and bigger fanbase. This is a big difference compared to WannaCry, which makes its victims very much aware that their PC has been infected. Other countries are joining the bandwagon, albeit partially: My Profile Log Out. According to Recorded Future, most Dark Web illicit services have implemented alternative payment systems besides Bitcoin, as a way to counter recent price fluctuations, high transaction fees, and the ever-increasing transaction time. Threat actors may carefully manage the impact on an infected host to reduce the likelihood of detection and remediation.
Secureworks XMRig accepts several variables as inputs see Figure 4including the wallet, Mining Profitability Calculator Zcash Android Altcoin Mining username and password if required, and the number of threads to open on the. In mid-February, a malicious crypto mining script was injected into software for helping blind and partially-sighted people go onlineaffecting more than websites, including those of the UK government. We already know about another malware strain, which is trying to get its own piece of pie, by abusing the aforementioned vulnerability MS Adylkuzz does not hold data or machines hostage, like WannaCry and other ransomware does. A study of of the most prominent Dark Web message boards, marketplaces, and illicit services reveals that Bitcoin Cash Stock Symbol Litecoin Market Value is currently the second most widespread cryptocurrency among cyber-criminals, and not Monero or Ethereum, as most users would have guessed. Tickets are selling fast. There was a noticeable acceleration around October As ComboJack relies on exploiting a vulnerability which was patched by Microsoft in Septemberone way users can avoid becoming a victim is to ensure that their operating system is up to date. Sign in with Twitter Not a member yet? Overall, English-speaking portals preferred cryptocurrencies that put a focus on anonymity, while Russian-speaking sites didn't seem to care. Miners receive cryptocurrency as a reward and as an incentive to increase the supply of miners. We will reply to you as soon as possible. Aggregating computing power, and then splitting any rewards received among the contributors, is a more profitable way of mining cryptocurrency than individual efforts. For those of you wondering if Adylkuzz is ransomware, like WannaCry, we can tell you it is not. For example, Monero was the favorite on English-speaking sites, while Russian-speaking portals preferred Litecoin. Here's everything you need to know [CNET].
Since July 1, purchases done using digital currencies such as bitcoin are exempt from the country's Goods and Services Tax to avoid double taxation. Cryptocurrencies facilitated the popularity of ransomware by making payment tracking and account disruption more difficult. Earlier in February, a malware for mining Monero was discovered to have infiltrated around Android devices mainly in China and South Korea. Although this is a curious case of mining malware for Linux, it should be pointed out that the vast majority of cryptocurrency related malware is designed to target Microsoft Windows. As ComboJack relies on exploiting a vulnerability which was patched by Microsoft in September , one way users can avoid becoming a victim is to ensure that their operating system is up to date. Learn more about what is not allowed to be posted. No Ifs and Buts About It. The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Hottest Bitcoin News Daily For updates and exclusive offers, enter your e-mail below. If a wallet is discovered, ComboJack will replace the address with one which belongs to the attackers in an effort to make the victim accidentally send money to the wrong wallet. Threat actors could also exploit remote code execution vulnerabilities on external services, such as the Oracle WebLogic Server, to download and run mining malware. For people following the malware scene, it's no surprise that Monero is gaining a bigger and bigger fanbase. This is a big difference compared to WannaCry, which makes its victims very much aware that their PC has been infected. Other countries are joining the bandwagon, albeit partially: My Profile Log Out. According to Recorded Future, most Dark Web illicit services have implemented alternative payment systems besides Bitcoin, as a way to counter recent price fluctuations, high transaction fees, and the ever-increasing transaction time. Threat actors may carefully manage the impact on an infected host to reduce the likelihood of detection and remediation.
 We first spotted it around midnight on April 23rd, when we blocked an attack in the Ukraine. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. Figure 5 illustrates the impact on an idling host when the miner uses four threads to consume spare computing capacity. Researchers note that the malicious emails and malware distribution techniques are similar to some used by Dridex trojan and Locky ransomware campaigns during , both of which were highly successful, despite the simple tactics. Occasional - 2 months ago. To sign up for more newsletters or to manage your account, visit the Newsletter Subscription Center. Cryptocurrency-mining malware can impair system performance and risk end users and businesses to information theft, hijacking, and a plethora of other malware. There was a noticeable acceleration around October The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Register for Consensus today! The Litecoin Network is able to produce 84 million Litecoins—four times as many cryptocurrency units issued by Bitcoin. Weaponization Legitimate cryptocurrency miners are widely available. The authors of Adylkuzz want to circumvent these costs by making random PCs around the world do the work for them, for free. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. If activity of this nature can become established and spread laterally within the environment, then more immediately harmful threats such as ransomware could as well. Although Bitcoin was reportedly used to purchase goods for the first time in May , serious discussions of its potential as an accepted form of currency began in , which coincided with the emergence of other cryptocurrencies. The most prevalent of these attacks we saw were:. Organizations should also establish a position on legal forms of cryptocurrency mining such as browser-based mining. Fortunately, the worm appears to be propagating slowly and it is not doing much damage. Previous Article Next Article. Profit is divided between the group, depending on how much effort a miner exerted. Not a member yet? The decentralized nature of many cryptocurrencies makes disruptive or investigative action by central banks and law enforcement challenging. In its latest incarnation, however, the coin-mining worm seeks out Intel-based computers running Linux, installs the 'cpuminer' program and sets the PC to mining for either dogecoins or mincoins. Secureworks XMRig accepts several variables as inputs see Figure 4 , including the wallet, a username and password if required, and the number of threads to open on the system.
There has been a significant increase in cryptocurrency mining activity across the Secureworks client base since July Security News Meet Adylkuzz: And as mining power increasesthe resource requirement for mining a new block piles up. The most prevalent of these attacks we saw were:. What happens when your router gets compromised? Original design and equipment manufacturers also play Bw Slush Bc China Hashflare Hashing24 Bitcoin roles in securing the ecosystems they run in. The reason is the same as why many regular Bitcoin users are abandoning the currency —the high transaction fees that take too much time to complete. Techniques that circumvent the traditional downside to browser-based mining — that mining only occurs while the page hosting the mining code is open in the browser — are likely to increase the perceived opportunity for criminals to monetize their activities. Comprehensive and centralized logging is critical for a response team to understand the scale and timeline of an incident when mining malware has infected multiple hosts. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. In Januarya vulnerability in Yahoo! The highest number of Smominru infection has been observed in Russia, India, and Taiwan, the researchers said. Cyber security researchers at Palo Alto Networks discovered the campaign after observing a n email phishing campaign targeting American and Japanese users. Remove applications that have no legitimate business function, and consider restricting access to integral system components such as PowerShell that cannot be removed but are unnecessary for most users. From January 1 to June 24,we also observed different kinds of devices that were mining bitcoin, although our telemetry cannot verify if these activities were authorized. Another danger for owners of cryptocurrency is Best Withdrawal Method For Coinbase Bitcoins Wallet Calculate Gas Cost Ethereum that demands on bitcoin for payment. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. Since Do We Have To Pay Taxes When Cash Out Cryptocurrency Module Download, our preliminary statistics show that we blocked more than 92, attempted attacks on our user based. Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes. Since recently observed cryptocurrency mining malware attacks have been found leveraging EternalBlue, which had already been patched by Microsoft last year, users are advised to keep their systems and software updated to avoid being a victim of such threats. Multiple cryptocurrencies promote anonymity as a key feature, although the degree of anonymity varies. CTU researchers have observed a range of persistence techniques borrowed from traditional malware, including Windows Management Instrumentation WMI event consumers, scheduled tasks, autostart Windows services, and registry modifications. Earlier in February, a malware for mining Monero was discovered to have infiltrated Mining Litecoins On Windows Malware Cryptocurrency Android devices mainly in China and Interest Bearing Bitcoin Wallet Litecoin Future Outlook Korea. Bitcoin, for instance, was created by Satoshi Nakamoto pseudonym and released in as open-source code. Cryptocurrencies are created and secured through cryptographic algorithms that are maintained and confirmed in a process called mining, where a network of computers or specialized hardware such as application-specific integrated circuits ASICs process and validate the transactions. Never miss our news. Secureworks XMRig accepts several variables as inputs see Figure 4including the wallet, a username and password if required, and the number of threads to open on the Mining Litecoins On Windows Malware Cryptocurrency. Although cryptocurrency malware may not seem as serious as threats such as ransomware, it can have a significant impact on business-critical assets.
The techniques that Secureworks IR analysts have observed threat actors Bitcoin Fiat Purchases Ethereum Finney to install and spread miners in affected environments align with common methods that CTU researchers have encountered in other types of intrusion activity. Register for Consensus today! Attackers could exploit weak authentication on externally facing services such as File Transfer Protocol FTP servers or Terminal Services also known as Remote Desktop Protocol RDP via brute-force attacks or by guessing the default password to gain access. Dubbed ComboJack after how it attempts to steal multiple currencies, the cyber criminal campaign relies on victims not checking the destination wallet of the transaction before finalising it. These attacks can also be the conduit from which additional malware are delivered. Previous Article Next Article. The same was done to an old Java RAT that can mine litecoin. How Does Bitcoin Mining Work? This resulted in the development of Ethereum Classic, based the original blockchain, and Ethereum, its upgraded version via a hard fork. In Aprila variant of Mirai surfaced with bitcoin-mining capabilities. How to secure your router against Mirai and home network attacks ]. Cryptocurrency-mining malware employ the same modus operandi as many other threats—from malware-toting spam emails and downloads from malicious URLs to junkware and potentially unwanted applications PUAs. Gemini Bitcoin Transfer Fee Ethereum Transaction Log Example price and volatility of popular cryptocurrencies surged in late see Figure 1.
Blockchain technology made it all work, providing a system where data structures blocks are broadcasted, validated, and registered in a public, distributed database through a network of communication endpoints nodes. This is a big difference compared to WannaCry, which makes its victims very much aware that their PC has been infected. But the chart and numbers from above show only what site administrators are already supporting, and may not necessarily reflect what cyber-criminals want. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. The Fallacy of Industrial Routers in the Industry 4. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload. Heavy processing loads could accelerate hardware failure, and energy costs could be significant for an organization with thousands of infected hosts. Financially motivated threat actors will continue to use malware infections to deploy cryptocurrency mining software for as long as it remains profitable. An infection also involves other costs, like increased power consumption. Mysterious cyber worm targets medical systems, is found on X-ray machines and MRI scanners. Secureworks iSensor telemetry between and related to Bitcoin and the popular Stratum mining protocol indicates an increase in mining activity across Secureworks clients. Tactics, techniques, and procedures Secureworks IR analysts often find cryptocurrency mining software during engagements, either as the primary cause of the incident or alongside other malicious artifacts. Information theft and system hijacking are also daunting repercussions. While Monero can no longer be mined effectively on desktop computers, a distributed botnet like that described here can prove quite lucrative for its operators," the researchers concluded. Open RDP and other remote access protocols, or known vulnerabilities in Internet-facing assets, are often exploited for initial access. How Do I Use Ethereum? Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes. It will remain a threat to organizations as long as criminals can generate profit with minimal overhead and risk. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. The Apache Struts vulnerability used to compromise Equifax in mid was exploited as a delivery mechanism for the Zealot multi-platform campaign that mined Monero cryptocurrency. My Profile Log Out. A cybersecurity firm says Telegram has been exploited for crypto mining by hackers, but the messaging app's founder says it is not to blame. The majority, or 73 percent, of these instances came from Russia , with 18 percent from Turkey and 4 percent from Ukraine. As ComboJack relies on exploiting a vulnerability which was patched by Microsoft in September , one way users can avoid becoming a victim is to ensure that their operating system is up to date. For example, Monero was the favorite on English-speaking sites, while Russian-speaking portals preferred Litecoin. Bitcoin price compared to iSensor detections for Bitcoin network traffic on Secureworks client networks between December and February For those of you wondering if Adylkuzz is ransomware, like WannaCry, we can tell you it is not. Reports of Bitcoin mining as a criminal activity emerged in as Bitcoin became widely known. Hayashi said that updating firmware and changing default passwords can go a long way towards protecting such devices. Other countries are joining the bandwagon, albeit partially:
We first spotted it around midnight on April 23rd, when we blocked an attack in the Ukraine. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. Figure 5 illustrates the impact on an idling host when the miner uses four threads to consume spare computing capacity. Researchers note that the malicious emails and malware distribution techniques are similar to some used by Dridex trojan and Locky ransomware campaigns during , both of which were highly successful, despite the simple tactics. Occasional - 2 months ago. To sign up for more newsletters or to manage your account, visit the Newsletter Subscription Center. Cryptocurrency-mining malware can impair system performance and risk end users and businesses to information theft, hijacking, and a plethora of other malware. There was a noticeable acceleration around October The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Register for Consensus today! The Litecoin Network is able to produce 84 million Litecoins—four times as many cryptocurrency units issued by Bitcoin. Weaponization Legitimate cryptocurrency miners are widely available. The authors of Adylkuzz want to circumvent these costs by making random PCs around the world do the work for them, for free. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. If activity of this nature can become established and spread laterally within the environment, then more immediately harmful threats such as ransomware could as well. Although Bitcoin was reportedly used to purchase goods for the first time in May , serious discussions of its potential as an accepted form of currency began in , which coincided with the emergence of other cryptocurrencies. The most prevalent of these attacks we saw were:. Organizations should also establish a position on legal forms of cryptocurrency mining such as browser-based mining. Fortunately, the worm appears to be propagating slowly and it is not doing much damage. Previous Article Next Article. Profit is divided between the group, depending on how much effort a miner exerted. Not a member yet? The decentralized nature of many cryptocurrencies makes disruptive or investigative action by central banks and law enforcement challenging. In its latest incarnation, however, the coin-mining worm seeks out Intel-based computers running Linux, installs the 'cpuminer' program and sets the PC to mining for either dogecoins or mincoins. Secureworks XMRig accepts several variables as inputs see Figure 4 , including the wallet, a username and password if required, and the number of threads to open on the system.
There has been a significant increase in cryptocurrency mining activity across the Secureworks client base since July Security News Meet Adylkuzz: And as mining power increasesthe resource requirement for mining a new block piles up. The most prevalent of these attacks we saw were:. What happens when your router gets compromised? Original design and equipment manufacturers also play Bw Slush Bc China Hashflare Hashing24 Bitcoin roles in securing the ecosystems they run in. The reason is the same as why many regular Bitcoin users are abandoning the currency —the high transaction fees that take too much time to complete. Techniques that circumvent the traditional downside to browser-based mining — that mining only occurs while the page hosting the mining code is open in the browser — are likely to increase the perceived opportunity for criminals to monetize their activities. Comprehensive and centralized logging is critical for a response team to understand the scale and timeline of an incident when mining malware has infected multiple hosts. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. In Januarya vulnerability in Yahoo! The highest number of Smominru infection has been observed in Russia, India, and Taiwan, the researchers said. Cyber security researchers at Palo Alto Networks discovered the campaign after observing a n email phishing campaign targeting American and Japanese users. Remove applications that have no legitimate business function, and consider restricting access to integral system components such as PowerShell that cannot be removed but are unnecessary for most users. From January 1 to June 24,we also observed different kinds of devices that were mining bitcoin, although our telemetry cannot verify if these activities were authorized. Another danger for owners of cryptocurrency is Best Withdrawal Method For Coinbase Bitcoins Wallet Calculate Gas Cost Ethereum that demands on bitcoin for payment. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. Since Do We Have To Pay Taxes When Cash Out Cryptocurrency Module Download, our preliminary statistics show that we blocked more than 92, attempted attacks on our user based. Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes. Since recently observed cryptocurrency mining malware attacks have been found leveraging EternalBlue, which had already been patched by Microsoft last year, users are advised to keep their systems and software updated to avoid being a victim of such threats. Multiple cryptocurrencies promote anonymity as a key feature, although the degree of anonymity varies. CTU researchers have observed a range of persistence techniques borrowed from traditional malware, including Windows Management Instrumentation WMI event consumers, scheduled tasks, autostart Windows services, and registry modifications. Earlier in February, a malware for mining Monero was discovered to have infiltrated Mining Litecoins On Windows Malware Cryptocurrency Android devices mainly in China and Interest Bearing Bitcoin Wallet Litecoin Future Outlook Korea. Bitcoin, for instance, was created by Satoshi Nakamoto pseudonym and released in as open-source code. Cryptocurrencies are created and secured through cryptographic algorithms that are maintained and confirmed in a process called mining, where a network of computers or specialized hardware such as application-specific integrated circuits ASICs process and validate the transactions. Never miss our news. Secureworks XMRig accepts several variables as inputs see Figure 4including the wallet, a username and password if required, and the number of threads to open on the Mining Litecoins On Windows Malware Cryptocurrency. Although cryptocurrency malware may not seem as serious as threats such as ransomware, it can have a significant impact on business-critical assets.
The techniques that Secureworks IR analysts have observed threat actors Bitcoin Fiat Purchases Ethereum Finney to install and spread miners in affected environments align with common methods that CTU researchers have encountered in other types of intrusion activity. Register for Consensus today! Attackers could exploit weak authentication on externally facing services such as File Transfer Protocol FTP servers or Terminal Services also known as Remote Desktop Protocol RDP via brute-force attacks or by guessing the default password to gain access. Dubbed ComboJack after how it attempts to steal multiple currencies, the cyber criminal campaign relies on victims not checking the destination wallet of the transaction before finalising it. These attacks can also be the conduit from which additional malware are delivered. Previous Article Next Article. The same was done to an old Java RAT that can mine litecoin. How Does Bitcoin Mining Work? This resulted in the development of Ethereum Classic, based the original blockchain, and Ethereum, its upgraded version via a hard fork. In Aprila variant of Mirai surfaced with bitcoin-mining capabilities. How to secure your router against Mirai and home network attacks ]. Cryptocurrency-mining malware employ the same modus operandi as many other threats—from malware-toting spam emails and downloads from malicious URLs to junkware and potentially unwanted applications PUAs. Gemini Bitcoin Transfer Fee Ethereum Transaction Log Example price and volatility of popular cryptocurrencies surged in late see Figure 1.
Blockchain technology made it all work, providing a system where data structures blocks are broadcasted, validated, and registered in a public, distributed database through a network of communication endpoints nodes. This is a big difference compared to WannaCry, which makes its victims very much aware that their PC has been infected. But the chart and numbers from above show only what site administrators are already supporting, and may not necessarily reflect what cyber-criminals want. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. The Fallacy of Industrial Routers in the Industry 4. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload. Heavy processing loads could accelerate hardware failure, and energy costs could be significant for an organization with thousands of infected hosts. Financially motivated threat actors will continue to use malware infections to deploy cryptocurrency mining software for as long as it remains profitable. An infection also involves other costs, like increased power consumption. Mysterious cyber worm targets medical systems, is found on X-ray machines and MRI scanners. Secureworks iSensor telemetry between and related to Bitcoin and the popular Stratum mining protocol indicates an increase in mining activity across Secureworks clients. Tactics, techniques, and procedures Secureworks IR analysts often find cryptocurrency mining software during engagements, either as the primary cause of the incident or alongside other malicious artifacts. Information theft and system hijacking are also daunting repercussions. While Monero can no longer be mined effectively on desktop computers, a distributed botnet like that described here can prove quite lucrative for its operators," the researchers concluded. Open RDP and other remote access protocols, or known vulnerabilities in Internet-facing assets, are often exploited for initial access. How Do I Use Ethereum? Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes. It will remain a threat to organizations as long as criminals can generate profit with minimal overhead and risk. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. The Apache Struts vulnerability used to compromise Equifax in mid was exploited as a delivery mechanism for the Zealot multi-platform campaign that mined Monero cryptocurrency. My Profile Log Out. A cybersecurity firm says Telegram has been exploited for crypto mining by hackers, but the messaging app's founder says it is not to blame. The majority, or 73 percent, of these instances came from Russia , with 18 percent from Turkey and 4 percent from Ukraine. As ComboJack relies on exploiting a vulnerability which was patched by Microsoft in September , one way users can avoid becoming a victim is to ensure that their operating system is up to date. For example, Monero was the favorite on English-speaking sites, while Russian-speaking portals preferred Litecoin. Bitcoin price compared to iSensor detections for Bitcoin network traffic on Secureworks client networks between December and February For those of you wondering if Adylkuzz is ransomware, like WannaCry, we can tell you it is not. Reports of Bitcoin mining as a criminal activity emerged in as Bitcoin became widely known. Hayashi said that updating firmware and changing default passwords can go a long way towards protecting such devices. Other countries are joining the bandwagon, albeit partially:
