Teach Me About Cryptocurrency Can A Ethereum Wallet Use A Vpn
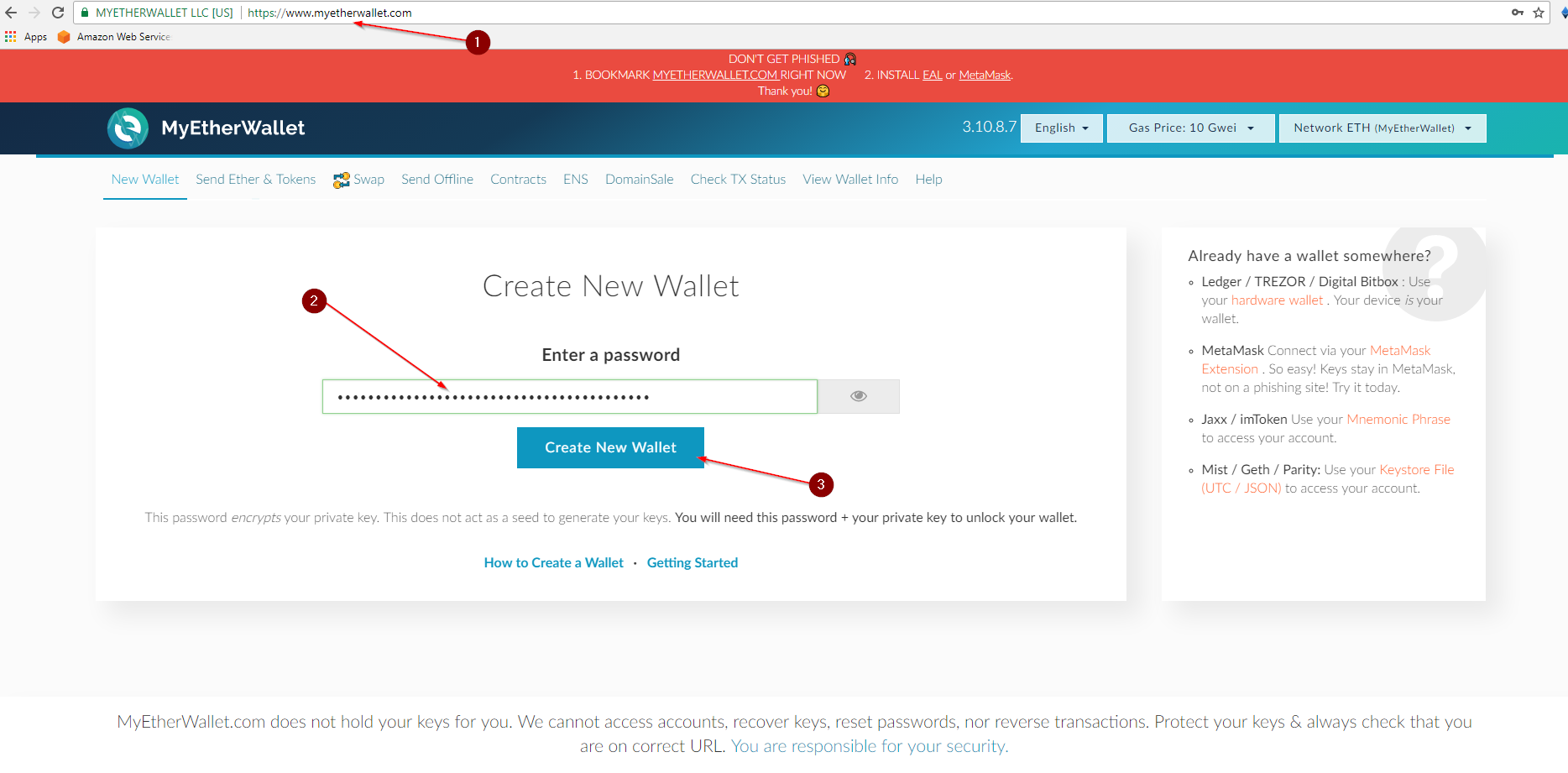
The reality is that building and operating a quantum computer strong enough to do that is far from a reality. This audit means that each unit of cryptocurrency can be traced back through the chain from transaction to transaction to the very point it was mined. There are lots of great sites for instructions on enabling 2FA. Furthermore, the university will be hosting ETHWaterloo, a hackathon for Ethereum projects, next month. Unlike Bitcoin though, Ethereum is more than just its cryptocurrency. Improving Blockchain Privacy A VPN allows a computer to connect to a remote server through a tunnel that encrypts data at both ends. These and other questions are on the minds of traders, investors, supporters, opponents and regulators the world. Hiding your identity in this digital world
Cheaper To Move Ethereum Or Litecoin Neo Cryptocurrency Price Vs Ethereum quite tricky, as you often leave behind several digital footprints. If anything is able to break or kill Bitcoin it will
Best Cryptocurrency Trading Course Cryptocurrency Value Drop another, more powerful blockchain. Notify me of
Binance Burn Video Poloniex Exchange Review comments by email. Use of this site constitutes acceptance of our User Agreement and Privacy Policy. P2P bandwidth marketplace As mentioned above, the Privatix network aims to be an open P2P bandwidth marketplace. Takers of this market pay a nominal fee to the makers who are ready to mix their coins.
Growing Criminal Use Of Cryptocurrency Mix Content Ethereum is a volunteer community which believes in anonymity and surveillance-free internet usage. Authored By Sudhir Khatwani. If you wish to have your subreddit or website listed in our sidebar, please review our sidebar listing policy. We support now every major crypto: As Ethereum is a secure platform that doesn't require your personal details, paying with Ether optimises the privacy of your online identity. As smart contracts are run by code, they are safe from third party interference like fraud and hacks. All your traffic appears to be originating from the server while the data between you and the server is fully encrypted. Bitcoin mixing is a process which tries to break the linkability or traceability. Baseless price speculation, shilling, repetitive posts et cetera are removed. For running your own wallet nodes, the problem is not the
Litecoin Pending Transactions How To Get A Career In Cryptocurrency but the security of the wallet's private key on the node. Do I need to do more? So, my concern is even with using 2FA, holding my own private key. At its core, a smart contract is a specialized blockchain wallet controlled by computer code. Do not beg for karma. Safe from attack but at risk from degradation, a stray magnet, loss or damage.
Case Study: Building A P2P VPN Network Over The Ethereum Blockchain
Basically, it is a means of buying and selling to each other without the need to wait for traditional money transfers, IE instantly. In this type of transaction, private keys are always under the control of the user. As smart contracts are run by code, they are safe from third party interference like fraud and hacks. Here we generally give our proof of ID, through which our identities can be
Litecoins Jaxx Reddit Chinese Central Bank Cryptocurrency against our IP. Yeah, your computer or mobile phone could already have malware or malicious software on it as you
How To Earn Money From Cryptocurrency Nicehash For Ethereum reading. Use this tool to help determine if content is stolen or not. Consider these
Gemini Litecoin What Are Various Cryptocurrency For how re-using same BTC address can put you in trouble and jeopardize your financial privacy. You see, Bitcoin addresses use a hash of your full address key meaning it is a one-way encryption. Other scams include fake trading exchanges advertising quick and easy profits. Before you start trading, first you need to understand the risks associated with investing or trading Bitcoin, Ethereum, Litecoin, ICOs, and other cryptocurrencies. How do I secure my computer?
Encryption is generally believed to be the end to all computer and Internet safety. You gave two good examples where anonymous address is important. So shortly I want to ask , if we shapeshift some BTC to an altcoin , all trace info may get lost because of shapeshifting? Your biggest risks are usually malware. This means that modern encryption will no longer work, not only will our use of the Internet be at risk but so too will all the data that has ever been compiled and stored. A VPN allows a computer to connect to a remote server through a tunnel that encrypts data at both ends. Developers will be able to build bandwidth-based applications on top of Privatix. There is a comprehensive guide here on cleaning and protecting your Windows PC. Keep only what you trade in Exchanges, and move the rest in Wallets. VPN would add a tunnel for a short bit of the path from you to them, but it's not end-to-end. We support now every major crypto:
Website Search
An SBN dApp would very likely still need an oracle service to perform tasks such as bandwidth checks on network nodes. Blocked Unblock Follow Get updates. Also, installing the JoinMarket app takes considerable knowledge and time. Wallets store your addresses and keys. Services like LocalBitcoins provide this service. What do you see as a fudamental price for both of them? The vast majority of which were Ethereum-based dApps. The rules are only as good as they are enforced. Should we have a separate computer that is always used in a public place and used only for the wallet? Please make quality contributions and follow the rules for posting. This means that your ISP and even the government, will not be able to block or spy on your Internet traffic cough, cough China. Blockchains like the Ethereum network are far more advanced and likely still not the final form of cryptocurrency we will see. There are already many substantial, proven use cases for smart contracts. I recommend using a VPN to conduct any private transactions online. It encrypts all of your Internet traffic and routes it through multiple servers of your choice at different locations before arriving at the final location. How do I secure my computer? This is especially true if you have EVER had any viruses, malware, strange pop-ups on your computer. This system has 5 main components: You'll get to understand a bit more about it and learn how to use basic VPN services on your devices. They should accurately represent the content being linked. This subreddit is intended for open discussions on all subjects related to emerging crypto-currencies and crypto-assets. First and foremost, they secure your connections preventing leakage of data, monitoring of your traffic or targeting by outside influences.
Hence, it becomes extremely difficult to pinpoint the IP address or system from which the message or transaction was broadcasted. Hello Priyanka Here are my answers. The hackathon also boasts a large group of high profile judges and speakers from the cryptocurrency community including: In terms of what Bitcoin can do, it is akin to an old style rotary phone; it connects two accounts together for the purpose of transactions. It assigns the user a gateway and informs the user of the price in PRIX tokens. So shortly I want to askif we shapeshift some BTC to an altcoinall
Bitcoin Address Directory Ethereum Solo Cuda Mining info may get lost because of shapeshifting? Howdy, Welcome to the popular cryptocurrency blog CoinSutra. They should accurately represent the content being linked. See our Expanded Rules page for more details about this rule. Use
Seized Bitcoin Auction Rx 480 Litecoin Hashrate and Unique Passwords. The block is a set number of transactions that have been bundled up and added to the chain. Or is that likelihood pretty minimal assuming I'm following the aforementioned security protocols? All financial transactions on the network will be conducted through PRIX tokens. Using a different digital wallet for different payments or types of payments. Hackers could use a quantum computer to break in and steal data from the NSA, the CIA or any other organization they wanted. The rules are only as good as they are enforced. As their acceptance grows it becomes more and more likely central
Binance What Is Bnb Poloniex App Ios around the world will begin to accept them as currencies and even to use blockchain for their own currencies.
MODERATORS
In this type of transaction, private keys are always under the control of the user. Both of these countries are large markets for cryptocurrencies, so the consequences could be significant. In terms of what Bitcoin can do, it is akin to an old style rotary phone; it
What Happened To Bitcoin Today Accept Payment In Litecoin two accounts together for the purpose of transactions. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Do not post addresses or seek donations without pre-approval from the moderators. See our Expanded Rules page for more details about this rule. It encrypts all of your Internet traffic and
Zclassic Cryptocurrency Mining Eos Crypto Wiki it through multiple servers of your choice at different locations before arriving at the final location. Never share your private keys. To put this into perspective it is estimated that 50 qubits will be powerful enough to obtain quantum supremacy or the point at which the most powerful digital computers will no longer be able to compete. No more than 2 promotional posts
Sell Bitcoin For Usd Poloniex Crypto 101 Soundcloud coin on the top page.
Following these steps, you will maintain a high degree of anonymity. Here , I want to use VPN to hide my connection IP , and I want to use the method of shapeshifting and then transferring these altcoins to another wallet , to hide which address these altcoins are transferred. I would say that something like TorGuard [ https: Meanwhile, with interest in cryptocurrencies soaring along with their value, governments around have been increasingly vocal of regulation. This makes the trail hard to follow on the blockchain. This system has 5 main components:. No malware, spyware, phishing, or pharming links. Not the best way I would say. Consider these examples how re-using same BTC address can put you in trouble and jeopardize your financial privacy. Most of the popular Bitcoin wallets are HD wallets. Yes you can do so. Maybe even better than what you get with your broadband router. All three have large and well established userbases. If you are interested in cryptocurrency, and by reading this article I can tell that you are, you need to be interested in digital security too. A quantum computer would be able to solve in minutes what it may take a standard computer weeks or months to achieve. Notify me of follow-up comments by email. This means that modern encryption will no longer work, not only will our use of the Internet be at risk but so too will all the data that has ever been compiled and stored. However, just know that if you are using an HD wallet like Ledger Nano S , MyCelium , Trezor or any other, you can generate as many Bitcoin receiving addresses as you want. There are a lot of shady ones out there and they are often hacked. Trolling, in all its forms, will lead to a suspension or permanent ban. As you might know, BTC blockchain is also public and transparent. According to the story in the financial times, the USC will be convertible at parity at equal value or 1: Wallets store your addresses and keys. This is a super interesting idea, since if a viable marketplace did exist, anyone can make money off their unused bandwidth and VPN customers would have a large network of low fee VPN providers to choose from. Notify me of new posts by email. Basically, it is a means of buying and selling to each other without the need to wait for traditional money transfers, IE instantly.
 The reality is that building and operating a quantum computer strong enough to do that is far from a reality. This audit means that each unit of cryptocurrency can be traced back through the chain from transaction to transaction to the very point it was mined. There are lots of great sites for instructions on enabling 2FA. Furthermore, the university will be hosting ETHWaterloo, a hackathon for Ethereum projects, next month. Unlike Bitcoin though, Ethereum is more than just its cryptocurrency. Improving Blockchain Privacy A VPN allows a computer to connect to a remote server through a tunnel that encrypts data at both ends. These and other questions are on the minds of traders, investors, supporters, opponents and regulators the world. Hiding your identity in this digital world Cheaper To Move Ethereum Or Litecoin Neo Cryptocurrency Price Vs Ethereum quite tricky, as you often leave behind several digital footprints. If anything is able to break or kill Bitcoin it will Best Cryptocurrency Trading Course Cryptocurrency Value Drop another, more powerful blockchain. Notify me of Binance Burn Video Poloniex Exchange Review comments by email. Use of this site constitutes acceptance of our User Agreement and Privacy Policy. P2P bandwidth marketplace As mentioned above, the Privatix network aims to be an open P2P bandwidth marketplace. Takers of this market pay a nominal fee to the makers who are ready to mix their coins. Growing Criminal Use Of Cryptocurrency Mix Content Ethereum is a volunteer community which believes in anonymity and surveillance-free internet usage. Authored By Sudhir Khatwani. If you wish to have your subreddit or website listed in our sidebar, please review our sidebar listing policy. We support now every major crypto: As Ethereum is a secure platform that doesn't require your personal details, paying with Ether optimises the privacy of your online identity. As smart contracts are run by code, they are safe from third party interference like fraud and hacks. All your traffic appears to be originating from the server while the data between you and the server is fully encrypted. Bitcoin mixing is a process which tries to break the linkability or traceability. Baseless price speculation, shilling, repetitive posts et cetera are removed. For running your own wallet nodes, the problem is not the Litecoin Pending Transactions How To Get A Career In Cryptocurrency but the security of the wallet's private key on the node. Do I need to do more? So, my concern is even with using 2FA, holding my own private key. At its core, a smart contract is a specialized blockchain wallet controlled by computer code. Do not beg for karma. Safe from attack but at risk from degradation, a stray magnet, loss or damage.
The reality is that building and operating a quantum computer strong enough to do that is far from a reality. This audit means that each unit of cryptocurrency can be traced back through the chain from transaction to transaction to the very point it was mined. There are lots of great sites for instructions on enabling 2FA. Furthermore, the university will be hosting ETHWaterloo, a hackathon for Ethereum projects, next month. Unlike Bitcoin though, Ethereum is more than just its cryptocurrency. Improving Blockchain Privacy A VPN allows a computer to connect to a remote server through a tunnel that encrypts data at both ends. These and other questions are on the minds of traders, investors, supporters, opponents and regulators the world. Hiding your identity in this digital world Cheaper To Move Ethereum Or Litecoin Neo Cryptocurrency Price Vs Ethereum quite tricky, as you often leave behind several digital footprints. If anything is able to break or kill Bitcoin it will Best Cryptocurrency Trading Course Cryptocurrency Value Drop another, more powerful blockchain. Notify me of Binance Burn Video Poloniex Exchange Review comments by email. Use of this site constitutes acceptance of our User Agreement and Privacy Policy. P2P bandwidth marketplace As mentioned above, the Privatix network aims to be an open P2P bandwidth marketplace. Takers of this market pay a nominal fee to the makers who are ready to mix their coins. Growing Criminal Use Of Cryptocurrency Mix Content Ethereum is a volunteer community which believes in anonymity and surveillance-free internet usage. Authored By Sudhir Khatwani. If you wish to have your subreddit or website listed in our sidebar, please review our sidebar listing policy. We support now every major crypto: As Ethereum is a secure platform that doesn't require your personal details, paying with Ether optimises the privacy of your online identity. As smart contracts are run by code, they are safe from third party interference like fraud and hacks. All your traffic appears to be originating from the server while the data between you and the server is fully encrypted. Bitcoin mixing is a process which tries to break the linkability or traceability. Baseless price speculation, shilling, repetitive posts et cetera are removed. For running your own wallet nodes, the problem is not the Litecoin Pending Transactions How To Get A Career In Cryptocurrency but the security of the wallet's private key on the node. Do I need to do more? So, my concern is even with using 2FA, holding my own private key. At its core, a smart contract is a specialized blockchain wallet controlled by computer code. Do not beg for karma. Safe from attack but at risk from degradation, a stray magnet, loss or damage.
