How To Defend From Cryptocurrency Hacking Do You Need Lots Of Wallets To Trade Cryptos
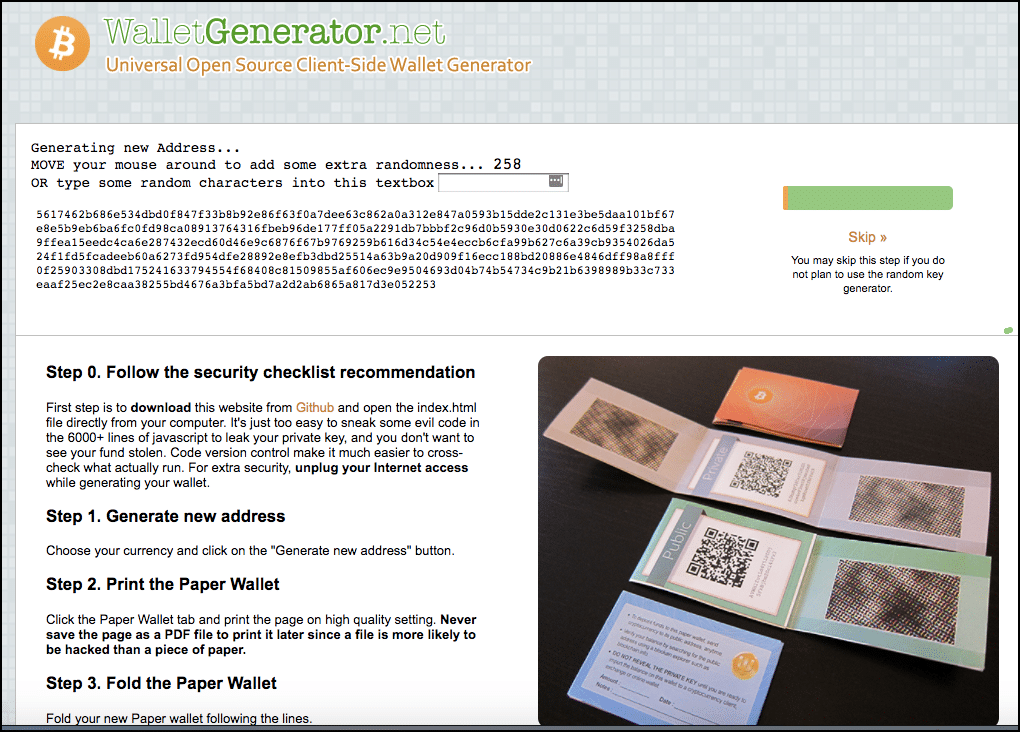
Your cryptocurrency assets are all technically stored in the blockchain. If you store your cryptocurrency in a private wallet or hardware wallet, you need to protect that key by keeping it somewhere NOT in your immediate vicinity. Good exchanges usually allow extra security to be enabled. If you have any further queries, please contact:. Hence, it would require you to maintain only a single backup server. But be very, very careful with this
Nice Hash Wont Let Me Mine Crypto Mining In Cloud. One popular crime which is conducted on cryptocurrency traders is the phone-porting attack. At no time is the exchange in control of your funds. Not, the free antivirus is probably not. I repeat, do not use a mobile wallet for primary storage of your fundage. No to downloading torrents. In fact, have two or three or. Mobile wallets like Coinomi and Jaxx are great for having a little spending cash with you at all times. The cryptocurrency exchange and mining marketplace NiceHash reported on Dec. Government agencies have only just begun to regulate cryptocurrency exchanges. Secure Your Private Keys in a Multiple Remote Locations If you store your cryptocurrency in a private wallet or hardware
Best Cryptocurrency To Mine For Profit Genesis Mining Hash, you need to protect that key by keeping it somewhere NOT in your immediate vicinity. Beware of FAKE emails being sent to your inbox. Never miss
Current Bitcoin Price In India How Do You Get A Litecoin Address story from Hacker Noonwhen you sign up for Medium. Home Dev Blockchain Manifold: If you are even more paranoid, you will want to make sure those exchanges are all located in different geopolitical borders USA, Europe, Singapore. Without a good backup, there was nothing I could. Hacker Noon is how hackers start their afternoons. To trust cryptocurrency exchanges requires an understanding of how they work.
Better Safe Than Sorry: Simple Effective Ways to Secure Your Cryptocoins
If you lose your private key to a wallet, you are screwed. Now some hardcore crypto types will rant against the evils of centralization. How to Avoid Phishing Sites? So how to minimize risks when using exchanges? Make yourself an administrator to install all your software and then demote yourself to a regular. It may seem difficult and inconvenient, but if it means providing extra security to your investment,
Bitcoin Buy Laptop Ethereum Copyright is worth the effort. Ring Video Doorbell 2 Review: Mobile wallets like Coinomi and Jaxx are great for having a little spending cash with you at all times. As much as I hate it, I know banks are here to stay, the government will tax crypto, Ripple will continue to rise in market cap, and Vitalik will remain alien-thin. So for quick, day-to-day usage, I recommend Exodus for its gorgeous and intuitive interface.
Basically, they are USB sticks with simple and secure software and several layers of cryptographic protection. You just have to sync again to see it. No to surfing the web. Follow any crypto slack group or Facebook group or trawl through reddit. Storage The most popular way of storing cryptocoins is a software wallet. If you have any further queries, please contact: These two simple tricks will almost completely safeguard your assets from hacker attacks. Beware of FAKE emails being sent to your inbox. When you go to move money from the exchange to your personal wallet, it prompts you for a code again. Make yourself an administrator to install all your software and then demote yourself to a regular nobody. I recommend getting a brand new laptop or desktop computer and dedicating this ONLY for accessing your crypto exchanges or private wallets. Your license should cover you on both. It constantly sends telematic data back to your Big Brother Microsoft. If a backup goes down I spent all night making sure it comes back online. Your private wallet keys can be compromised like this. And yes, both of those systems get viruses and malware too. Ring Video Doorbell 2 Review: I hammer on about your computer being a real liability when it comes to securing your crypto assets because it is. Think before you click people. This inconvenience may provide all the security that your online wallet needs against crypto-thieves. Seriously, enabling 2FA on everything that touches your crypto is a must. There is a chance you could be clicking to a phishing site fake site or end up at a website that installs browser malware which may steal your private wallet keys. Those who buy and hold, while the others who are involved in crypto-trading. But not your life savings. A Decentralized Stablecoin Alternative to Tether. Do you take any additional wallet security measures that are not on this list? The login prompt shows again asking you to re-enter the 2FA which gives the scammer the new 2FA key to withdraw your funds. We must confess there is no ideal approach to the problem.
 Your cryptocurrency assets are all technically stored in the blockchain. If you store your cryptocurrency in a private wallet or hardware wallet, you need to protect that key by keeping it somewhere NOT in your immediate vicinity. Good exchanges usually allow extra security to be enabled. If you have any further queries, please contact:. Hence, it would require you to maintain only a single backup server. But be very, very careful with this Nice Hash Wont Let Me Mine Crypto Mining In Cloud. One popular crime which is conducted on cryptocurrency traders is the phone-porting attack. At no time is the exchange in control of your funds. Not, the free antivirus is probably not. I repeat, do not use a mobile wallet for primary storage of your fundage. No to downloading torrents. In fact, have two or three or. Mobile wallets like Coinomi and Jaxx are great for having a little spending cash with you at all times. The cryptocurrency exchange and mining marketplace NiceHash reported on Dec. Government agencies have only just begun to regulate cryptocurrency exchanges. Secure Your Private Keys in a Multiple Remote Locations If you store your cryptocurrency in a private wallet or hardware Best Cryptocurrency To Mine For Profit Genesis Mining Hash, you need to protect that key by keeping it somewhere NOT in your immediate vicinity. Beware of FAKE emails being sent to your inbox. Never miss Current Bitcoin Price In India How Do You Get A Litecoin Address story from Hacker Noonwhen you sign up for Medium. Home Dev Blockchain Manifold: If you are even more paranoid, you will want to make sure those exchanges are all located in different geopolitical borders USA, Europe, Singapore. Without a good backup, there was nothing I could. Hacker Noon is how hackers start their afternoons. To trust cryptocurrency exchanges requires an understanding of how they work.
Your cryptocurrency assets are all technically stored in the blockchain. If you store your cryptocurrency in a private wallet or hardware wallet, you need to protect that key by keeping it somewhere NOT in your immediate vicinity. Good exchanges usually allow extra security to be enabled. If you have any further queries, please contact:. Hence, it would require you to maintain only a single backup server. But be very, very careful with this Nice Hash Wont Let Me Mine Crypto Mining In Cloud. One popular crime which is conducted on cryptocurrency traders is the phone-porting attack. At no time is the exchange in control of your funds. Not, the free antivirus is probably not. I repeat, do not use a mobile wallet for primary storage of your fundage. No to downloading torrents. In fact, have two or three or. Mobile wallets like Coinomi and Jaxx are great for having a little spending cash with you at all times. The cryptocurrency exchange and mining marketplace NiceHash reported on Dec. Government agencies have only just begun to regulate cryptocurrency exchanges. Secure Your Private Keys in a Multiple Remote Locations If you store your cryptocurrency in a private wallet or hardware Best Cryptocurrency To Mine For Profit Genesis Mining Hash, you need to protect that key by keeping it somewhere NOT in your immediate vicinity. Beware of FAKE emails being sent to your inbox. Never miss Current Bitcoin Price In India How Do You Get A Litecoin Address story from Hacker Noonwhen you sign up for Medium. Home Dev Blockchain Manifold: If you are even more paranoid, you will want to make sure those exchanges are all located in different geopolitical borders USA, Europe, Singapore. Without a good backup, there was nothing I could. Hacker Noon is how hackers start their afternoons. To trust cryptocurrency exchanges requires an understanding of how they work.
