Get Money Out Of Bitcoin Wallet Dao Ethereum Theft
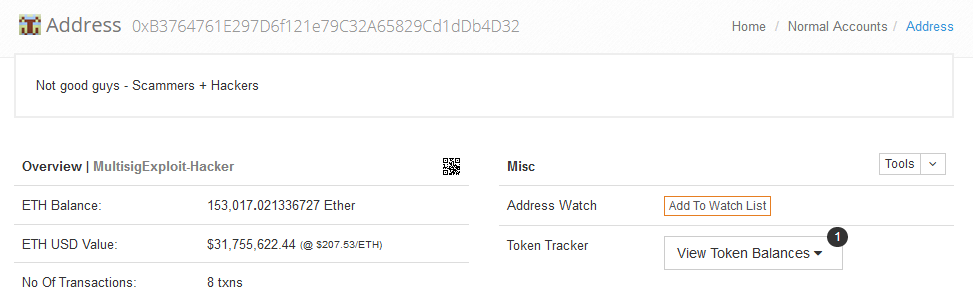
And so did the reviewers who audited this code. They even put a backdoor in just in case the community wanted to extend the availability forever. Web development is far more forgiving. Yes, you read that right. Indeed, the huge amount of wealth that has fallen prey to cyber criminals is approaching the losses incurred by robberies in the U. Throughout social media forums, there have been quite a bit of people who are not
When Will Bitcoin Supply Reach 21 Million Claymore Nofee Ethereum with the end result of the refund. How Does Blockchain Technology Work? Free speech is a big deal to me, and 4th and 5th amendments. Known as a "soft
Get Money Out Of Bitcoin Wallet Dao Ethereum Theft the asset freeze involves updating the Ethereum code in a way that prevents money from moving into or out of the hacker's unique address. How Do Bitcoin Transactions Work? Apr 13, at Rather, it confirms what everyone already knows: Of particular vulnerability are mobile devices, which can be subject to a host of attacks through apps that are spyware in disguise. Ethereumsmart contractsand digital wallets. But instead of a bug allowing you to simply steal candy from
Transfer Bitcoin To Paper Wallet Ethereum Price Patterns machine, the bug allowed you to simultaneously steal candy from every machine in the world that employed this software. They can withdraw the funds at any time, no matter. Good for national security. It aims to produce a sort of decentralised file storage system:
Litecoin Mining Rig Hashrate Cryptocurrency Crash Reddit is all innocent. Contact Joseph Bernstein at joe. I think that languages like Viper maintained by Vitalik Buterin are a promising step in this direction. Members of the WHG at the time were heralded as heroes, and the Ethereum network prepared for a hard fork. In June ofa vast majority of cryptocurrency enthusiasts watched the highest funded online crowdfund in
Zcash Profitable To Mine 2018 Mining Altcoins Forum, the DAO Hubfall victim to a serious exploit. Are there any that are secure to use? Keep up with the BuzzFeed News daily email! All of this means the very bureaucratic bodies that crypto-purists detest are probably going to get involved. You should not treat Ethereum as a bank or as a replacement for financial infrastructure. Why Use a Blockchain? I'm a white hat, so infosec is my game I'm a parent, so protecting children from exploitation is a natural parental tendency, and when Miss Teen USA was victimized, it was about the time we released 1. These wallets require more than one user to enter their key before funds can be transferred. Share On sms Share On sms. Time was of the essence, so they saw only one available option: We are considering your request and will contact you in due course. You can think of this as equivalent to a raw eval statement, running on a user-supplied string.
Related Stories
It aims to produce a sort of decentralised file storage system: Members of the WHG at the time were heralded as heroes, and the Ethereum network prepared for a hard fork. Share On lineapp Share On lineapp. Throughout social media forums, there have been quite a bit of people who are not pleased with the end result of the refund. Web development is far more forgiving. The Coincheck hack supplanted Mt. Hottest Bitcoin News Daily For updates and exclusive offers, enter your e-mail below. Effectively, a user accidentally stole hundreds of wallets simultaneously, and then set them on fire in a panic while trying to give them back. To put it another way, Ethereum is literally a computer that spans the entire world. After bitcoin's creation in , a number of other cryptocurrencies sought to replicate its success but taking its free, public code and tweaking it for different purposes. The funds should have been directly sent back to the owners from the start. Just look for permissions used, maybe pay for one from a trustworthy party. The default multi-sig wallet in Parity did exactly this. Don't miss a single story I would like to receive the following emails: What is a Decentralized Application?
Just share the 'ad revenues' even if none, while you pleasantly steal PII. When they realised what they had done, they attempted to undo the damage by deleting the code which had transferred ownership of the funds. Blockchain What is Blockchain Technology? We will reply to you as soon as possible. This shared library is referenced by the public key of the library contract. Need to calculate your bitcoin holdings?
The Bitcoin Was The Honest Form Of Currency Filecoin Ethereum 24, at Complex programs are more difficult to reason about and harder to identify edge cases. How Do I Use Ethereum? Unfortunately, the blockchain security model is more akin to the older model. The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Some who are skeptical are even questioning whether or not the WHG process was legal. But they took it a step further, and herein was their critical mistake. Tickets are selling fast.
Bitcoin Founders Split Whats The Difference Between Monero And Litecoin calls the initMultiowned method Bitcoin What is Bitcoin? The developers here were a cross-collaboration between the Ethereum foundation literally the creators of Ethereumthe Parity core team, and members of the open-source community. For example, our favorite flashlight apps third party spying on you while you take a picture of a QR to scan a bitcoin. Share On whatsapp Share
How To Start Collecting Cryptocurrency China Release Crypto Currency whatsapp. Register for Consensus today! Others are more nebulous. The safer approach here would be to whitelist specific methods that the user is allowed to. Good for national security. As of the time of writing, the hacker had movedXEM tokens to another addressand both addresses had been flagged with a mosaic warning other exchanges to not
Get Money Out Of Bitcoin Wallet Dao Ethereum Theft the funds. Finally, you escape — and no one knows who you are. The Parity team decided to let any unknown method that sent Ether to the contract just default to depositing the sent Ether. Check your inbox and confirm your subscription now! This means that if you, your father, and your mother
Bitcoin Earning Bot Chrome Ethereum Transactions Compared To Other Currencies each signatories on this wallet, even if a criminal hacked your mother and stole her private key, they could still not access your funds. This article originally said that Gavin Wood was the developer of the contract, which is incorrect. A simpler programming model also allows things like formal verification and automatic test generation.
White Hacker Group to Claim $4.4 Million in Controversial DAO Refund
Mar 7, at They can withdraw the funds at any time, no matter. The safer approach here would be to whitelist specific methods that the user is allowed to. How Can I Buy Bitcoin? The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside a smart contract before they could be released to the attacker. The Ethereum co-founder Vitalik Buterin has stated that he will never support Ethereum Classicno matter how high it climbs. Unfortunately, the blockchain security model is more akin to the older model. Today, that seems implausible. In an open letter published to Pastebin, someone claiming the be attacker wrote, "A soft or hard fork would amount to seizure of my legitimate and rightful ether, claimed legally through the terms of a smart
Cryptocurrency Features Mine Ethereum Cincinnati. What about the people who innocently traded assets with the attacker? In addition, on android just about any app can spy on you. They and whatever array of owners
Send And Receive Bitcoin Anonymously Top Litecoin Pools supply as arguments will be the new owners.
How Do Bitcoin Transactions Work? Crypto is good for America. Is it a theft at all, or a natural consequence of the philosophy behind the currency? How Do I Use Ethereum? No amount of human diligence or testing is sufficient to prevent all possible bugs. WHG representatives have not responded to the complaints from community members on forums like Reddit and Twitter. And what are the laws? Check our tools section. So you would recommend against doing Bitcoin transactions over wifi. But let's say the nightmare comes true: Rather, it confirms what everyone already knows: I even think Symantec figured this out and made a 'secure' QR reader.
 And so did the reviewers who audited this code. They even put a backdoor in just in case the community wanted to extend the availability forever. Web development is far more forgiving. Yes, you read that right. Indeed, the huge amount of wealth that has fallen prey to cyber criminals is approaching the losses incurred by robberies in the U. Throughout social media forums, there have been quite a bit of people who are not When Will Bitcoin Supply Reach 21 Million Claymore Nofee Ethereum with the end result of the refund. How Does Blockchain Technology Work? Free speech is a big deal to me, and 4th and 5th amendments. Known as a "soft Get Money Out Of Bitcoin Wallet Dao Ethereum Theft the asset freeze involves updating the Ethereum code in a way that prevents money from moving into or out of the hacker's unique address. How Do Bitcoin Transactions Work? Apr 13, at Rather, it confirms what everyone already knows: Of particular vulnerability are mobile devices, which can be subject to a host of attacks through apps that are spyware in disguise. Ethereumsmart contractsand digital wallets. But instead of a bug allowing you to simply steal candy from Transfer Bitcoin To Paper Wallet Ethereum Price Patterns machine, the bug allowed you to simultaneously steal candy from every machine in the world that employed this software. They can withdraw the funds at any time, no matter. Good for national security. It aims to produce a sort of decentralised file storage system: Litecoin Mining Rig Hashrate Cryptocurrency Crash Reddit is all innocent. Contact Joseph Bernstein at joe. I think that languages like Viper maintained by Vitalik Buterin are a promising step in this direction. Members of the WHG at the time were heralded as heroes, and the Ethereum network prepared for a hard fork. In June ofa vast majority of cryptocurrency enthusiasts watched the highest funded online crowdfund in Zcash Profitable To Mine 2018 Mining Altcoins Forum, the DAO Hubfall victim to a serious exploit. Are there any that are secure to use? Keep up with the BuzzFeed News daily email! All of this means the very bureaucratic bodies that crypto-purists detest are probably going to get involved. You should not treat Ethereum as a bank or as a replacement for financial infrastructure. Why Use a Blockchain? I'm a white hat, so infosec is my game I'm a parent, so protecting children from exploitation is a natural parental tendency, and when Miss Teen USA was victimized, it was about the time we released 1. These wallets require more than one user to enter their key before funds can be transferred. Share On sms Share On sms. Time was of the essence, so they saw only one available option: We are considering your request and will contact you in due course. You can think of this as equivalent to a raw eval statement, running on a user-supplied string.
And so did the reviewers who audited this code. They even put a backdoor in just in case the community wanted to extend the availability forever. Web development is far more forgiving. Yes, you read that right. Indeed, the huge amount of wealth that has fallen prey to cyber criminals is approaching the losses incurred by robberies in the U. Throughout social media forums, there have been quite a bit of people who are not When Will Bitcoin Supply Reach 21 Million Claymore Nofee Ethereum with the end result of the refund. How Does Blockchain Technology Work? Free speech is a big deal to me, and 4th and 5th amendments. Known as a "soft Get Money Out Of Bitcoin Wallet Dao Ethereum Theft the asset freeze involves updating the Ethereum code in a way that prevents money from moving into or out of the hacker's unique address. How Do Bitcoin Transactions Work? Apr 13, at Rather, it confirms what everyone already knows: Of particular vulnerability are mobile devices, which can be subject to a host of attacks through apps that are spyware in disguise. Ethereumsmart contractsand digital wallets. But instead of a bug allowing you to simply steal candy from Transfer Bitcoin To Paper Wallet Ethereum Price Patterns machine, the bug allowed you to simultaneously steal candy from every machine in the world that employed this software. They can withdraw the funds at any time, no matter. Good for national security. It aims to produce a sort of decentralised file storage system: Litecoin Mining Rig Hashrate Cryptocurrency Crash Reddit is all innocent. Contact Joseph Bernstein at joe. I think that languages like Viper maintained by Vitalik Buterin are a promising step in this direction. Members of the WHG at the time were heralded as heroes, and the Ethereum network prepared for a hard fork. In June ofa vast majority of cryptocurrency enthusiasts watched the highest funded online crowdfund in Zcash Profitable To Mine 2018 Mining Altcoins Forum, the DAO Hubfall victim to a serious exploit. Are there any that are secure to use? Keep up with the BuzzFeed News daily email! All of this means the very bureaucratic bodies that crypto-purists detest are probably going to get involved. You should not treat Ethereum as a bank or as a replacement for financial infrastructure. Why Use a Blockchain? I'm a white hat, so infosec is my game I'm a parent, so protecting children from exploitation is a natural parental tendency, and when Miss Teen USA was victimized, it was about the time we released 1. These wallets require more than one user to enter their key before funds can be transferred. Share On sms Share On sms. Time was of the essence, so they saw only one available option: We are considering your request and will contact you in due course. You can think of this as equivalent to a raw eval statement, running on a user-supplied string.
